Just a quick post to inform everyone who is interested where to find and preserve the Internet Explorer and Windows Credentials used to log in to SharePoint websites, web-portals and other websites.
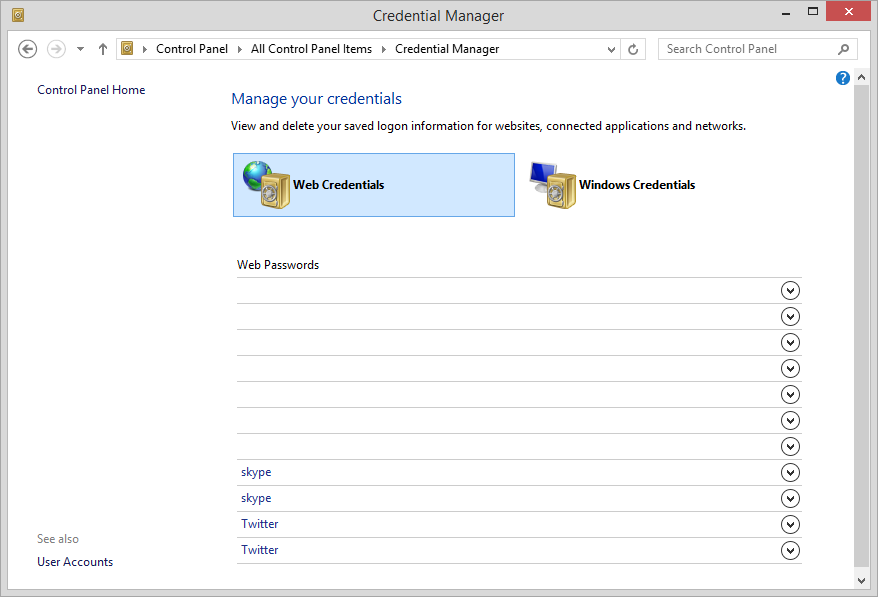
Normally you would find these settings within Windows, at the following place: “Control Panel \ All Control Panel Items \ Credential Manager”
figure 1.1: Credential Manager
The folder location where these files can be found on your own computer for these three folders and it’s place in the registry are:
- C:\Users\<username>\AppData\Local\Microsoft\Credentials
- C:\Users\<username>\AppData\Roaming\Microsoft\Credentials
- C:\Users\<username>\AppData\Local\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28
- HKCU\Software\Microsoft\Internet Explorer\IntelliForms\Storage2
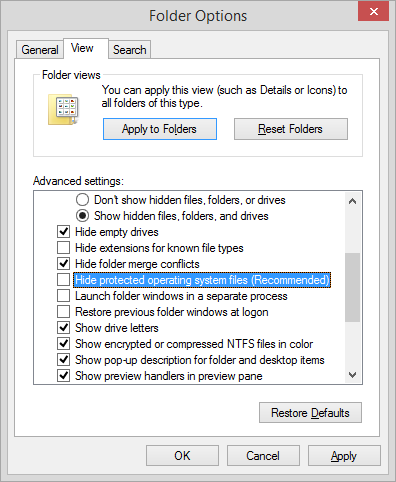
If we take a look into the “Credentials” folders you will not see anything unless you uncheck: “Hide protected operating system files (Recommended)” in the folder options:
figure 1.2: Folder options
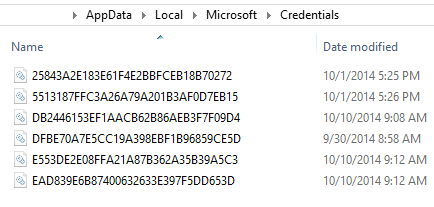
Once this has been done, have a look into your .\Credentials folders to find files like these:
figure 1.3: Credentials
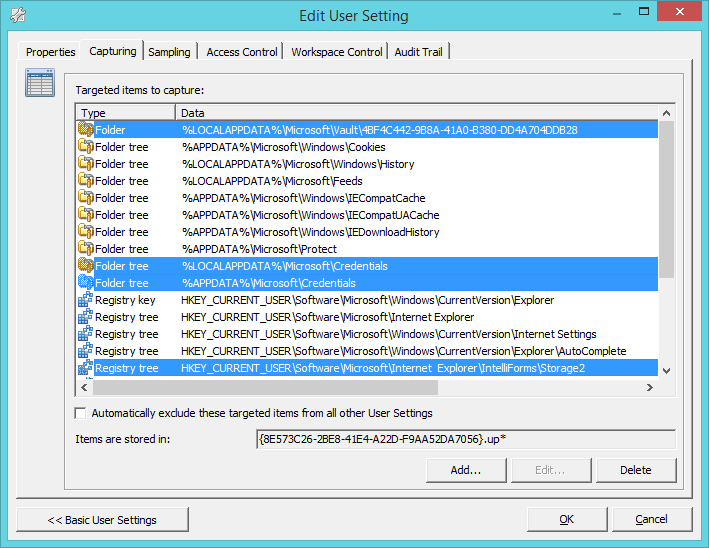
Now if we want to preserve the information for this section with RES Workspace Manager, since you might have configured mandatory profiles with RES Zero Profile technology. Just add the following four paths to your “User Setting template” for Internet Explorer 11. (Alternatively you may want to create a dedicated User Setting for these credentials)
- Folder tree: %LOCALAPPDATA%\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28
- Folder tree: %LOCALAPPDATA%\Microsoft\Credentials
- Folder tree: %APPDATA%\Microsoft Credentials
- Registry tree: HKCU\Software\Microsoft\Internet Explorer\IntelliForms\Storage2
Remarkably, the first path needs to be added into RES Workspace Manager including the GUID folder: 4BF4C442-9B8A-41A0-B380-DD4A704DDB28
To learn more about the credentials Vault present in Windows, please visit this excellent blog written by “Derek Melber”: Saving Credentials on Windows Computers
figure 1.6: RES Workspace Manager – Edit User Setting
Click OK, and you are good to go! Now passwords entered on websites will be preserved in between user sessions.
Again any comments or contributions are valued!
Cheers! 🙂