Today I was at a client which had a question among others about blocking the automatic installation of Internet Explorer 11.0 on clients which needed to run on Internet Explorer 8.0 only.
I was there integrating some new things in MDT when the question came from the person responsible for deploying the machines at their site. Since the company was not running WSUS and had not configured GPO’s to regulate Windows Updates. I needed to find another solution to prevent the automatic installation of any Internet Explorer version higher then 8.0.
While already made a regshot of a machine where I chose to hide the installation of Internet Explorer 9.0, 10.0 and 11.0, I struck a Microsoft link which referred to: Toolkit to Disable Automatic Delivery of Internet Explorer ##
It appears Microsoft has a toolkit, or set of scripts and files to do just that! 😀
You can find the toolkits for each version here:
Internet Explorer 7.0
Internet Explorer 8.0
Internet Explorer 9.0
Internet Explorer 10.0
Internet Explorer 11.0
Basically each ‘Toolkit’, exists out of the following set of files:
- IE##_Blocker.adm
which holds the GPO template to regulate the exact same thing via GPO - IE##_Blocker.cmd
which is an command line tool which writes specific values to the registry of the machine on which it is being executed - IE##_BlockerHelp.htm
which is the help file where you may find usefull information on how to use this tool
figure 1.1: the containing files of the IE##_BlockerToolkit.exe
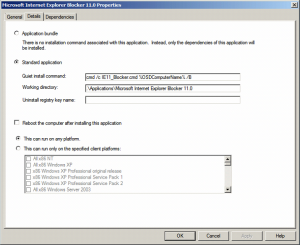
Now to prevent the installation of any unwanted version of Internet Explorer during your deployment process (when your machine is already running Windows and is connected to the internet, the polling for new updates starts right away). Just incorporate the IE##_Blocker.cmd as an application with source files into MDT.
figure 1.2: General application properties of the Microsoft Internet Explorer Blocker ##
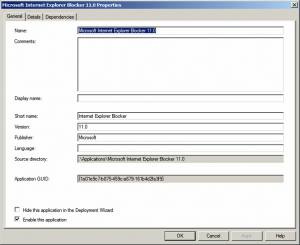
figure 1.3: Detailed application properties of the Microsoft Internet Explorer Blocker ##
Basically all that needs to be specified in the command line is the following: cmd /c IE##_Blocker.cmd %OSDComputerName% /B
cmd /c makes sure, that a command line is executed, IE##_Blocker.cmd speaks for itself, and since the variable %OSDComputerName% is known for the length of the deployment it can be used instead of the real hostname, and the /B switch tells the CMD to make a registry key into the registry to block the automatic installation of Internet Explorer.
When the machine is finished, a simple verification if the tool has been executed correctly will suffice:
figure 1.4: Registry key written that blocks the automatic installation of Internet Explorer
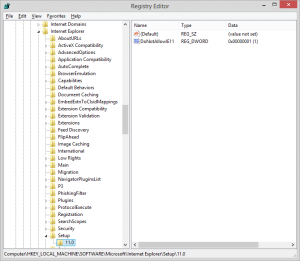
As you can see for each version of Internet Explorer a DWORD “DoNotAllowIE##” will be written with a value of “1” under: HKLM:Software\Microsoft\Internet Explorer\Setup\##.#\
Alternatively you may choose to write this regkey yourself, automated via a script, command line etc. do it via GPO, or implement Windows Server Update Services.
Hope you find this blog usefull, and if there is anything that you would like to ask or contribute, as always don’t hesitate to leave something in the comment section. 🙂