Working in real life production environments beats concept and test environments each and every time when it comes to debugging and optimizing the environment for your care-free 😉 end-users.
No matter how much you have tested up front, If you think you’ve got it covered for 99,9 % there’s always that 0,01 % that comes knocking at your door. This time it’s Internet Explorer 11 Enterprise Mode, in combination with Citrix XenApp 7.5 / 7.6 that causes a malfunction of the so called EMIE feature.
First some more details about Internet Explorer Enterprise Mode or EMIE:
A lot has been written about EMIE and one of the founding father’s I believe is Microsoft Architect Chris Jackson, who was so kind to at least hear me out after I contacted him on twitter FTW!
EMIE operates as an alternative to Internet Explorer’s Compatibility View. It’s a feature that needs to be enabled trough Group Policy Objects to reveal itself to the user. The benefit of using EMIE above Compatibility View is that EMIE allows us to specify individual websites to run EMIE even when the parenting website should not run EMIE. Opposed to Compatibility View, which allows you to only run entire domains in compatibility view, not excluding or including sub-domains or sub-sites.
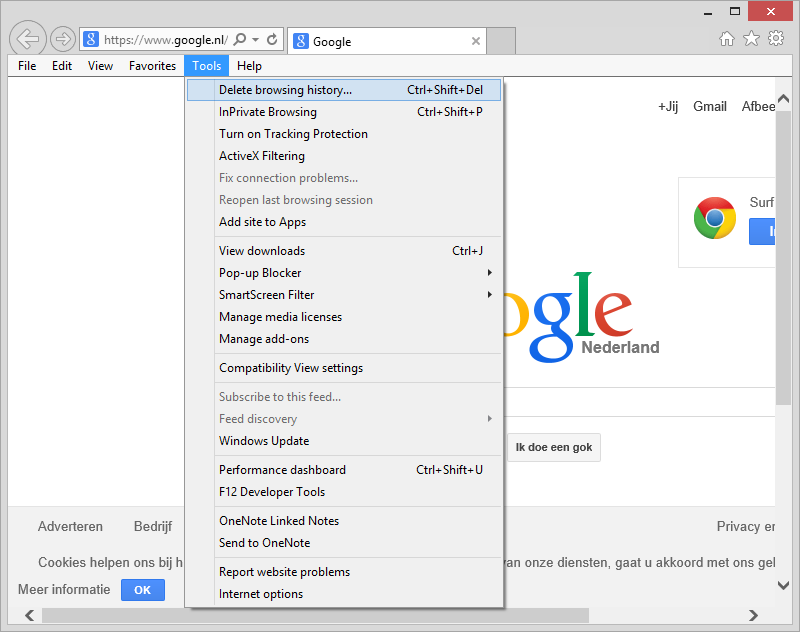
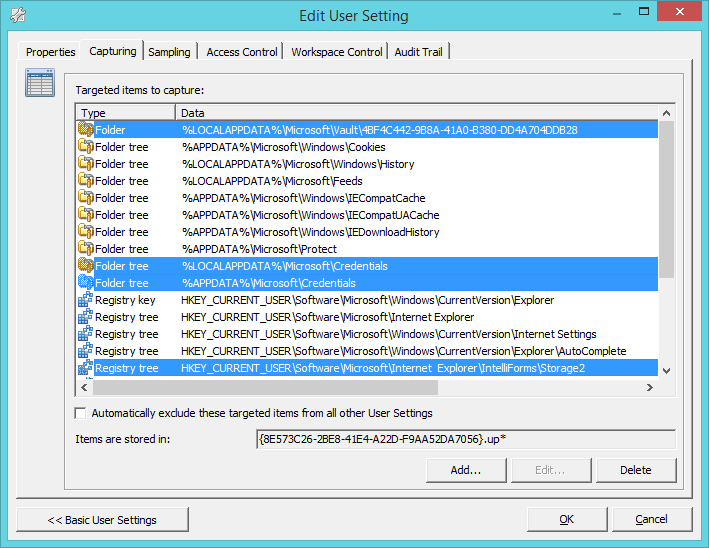
If EMIE would have been enabled on your machine, you would have found it here:
figure 1.1: Internet Explorer Tools
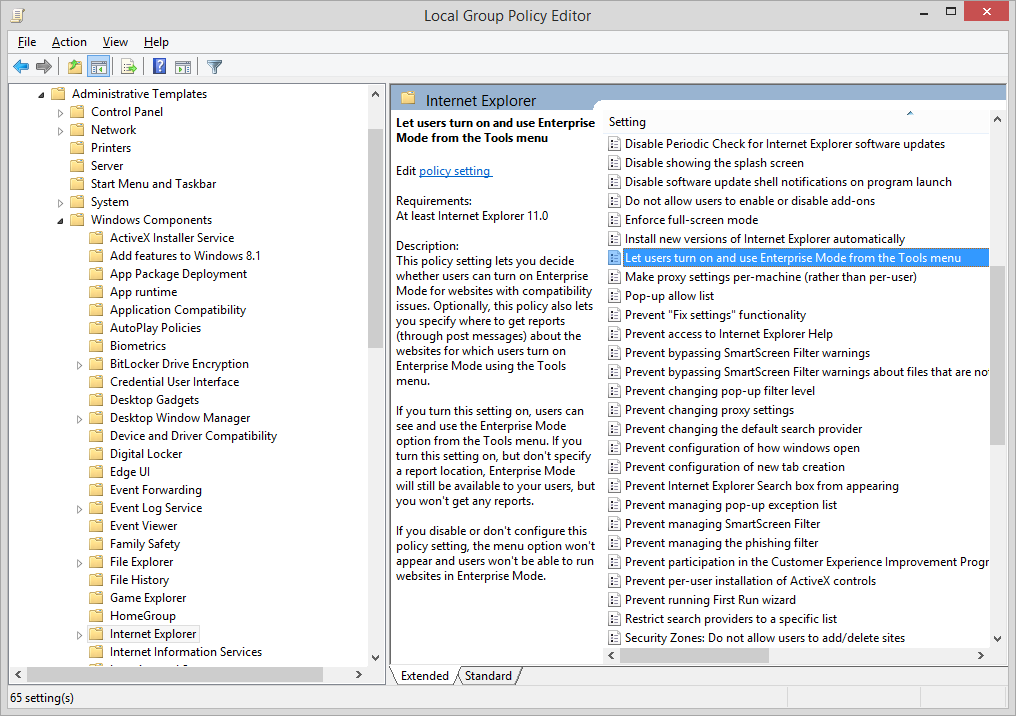
Since it’s not there we need to make it visible, start GPEDIT.MSC and go to: “Computer Configuration \ Administrative Templates \ Windows Components \ Internet Explorer” and enable “Let users turn on and use Enterprise Mode from the Tools menu“. Next, perform a GPUPDATE /FORCE to force the policy to become active.
figure 1.2: Group Policy Objects – Configure EMIE
This causes you to put websites in Enterprise Mode for the length of your current browser session. When you close your session, Enterprise Mode for this particular website isn’t active anymore when the website is revisited.
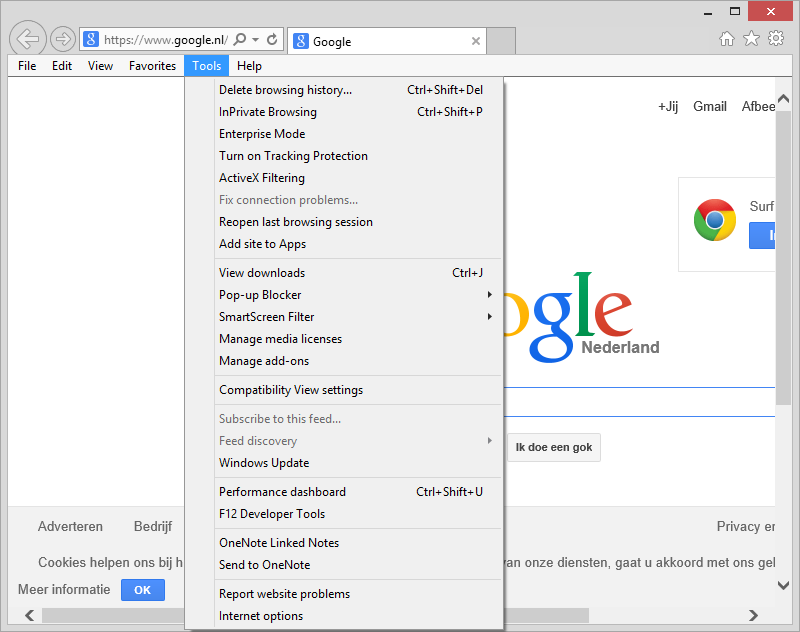
Since we configured the Group Policy Object, we can now see EMIE in Internet Explorer 11:
figure 1.3: Internet Explorer Tools – EMIE visible
Microsoft has come up with a solution to provide a list of websites that forces Internet Explorer 11 to always render those particular websites in Enterprise Mode. Therefore the following Group Policy Object is configured: “Computer Configuration \ Administrative Templates \ Windows Components \ Use the Enterprise Mode IE website list “. This allows you to generate a website list XML file, which contains which websites should run Enterprise Mode and which shouldn’t.
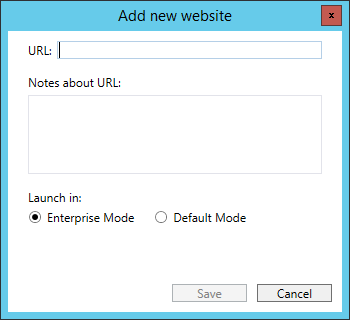
It looks like this, and is best managed and generated with the Enterprise Mode Site List Manager:
figure 1.4: EMIE Site List Manager
figure 1.5: EMIE Site List Manager – Add new website
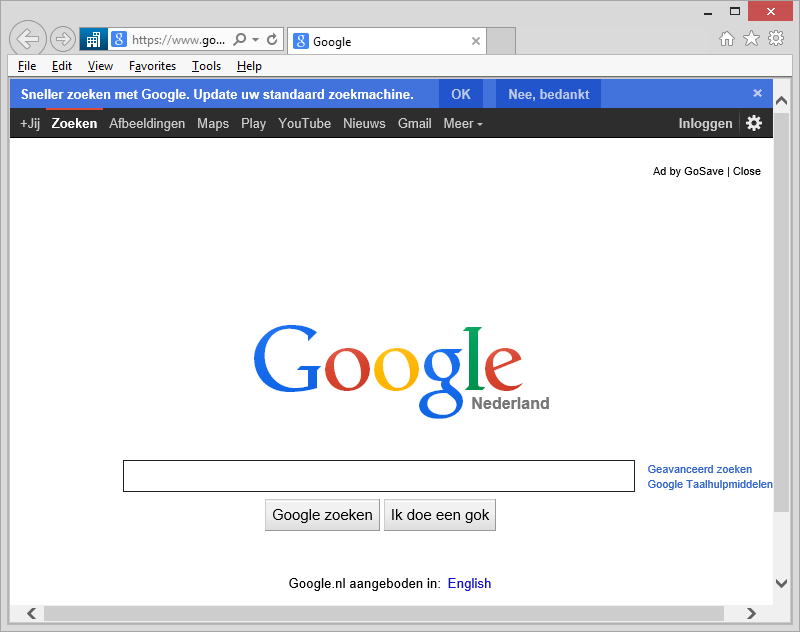
If for example the website: www.google.com was to run in Enterprise Mode, it would look like this:
figure 1.6: Google running EMIE
EMIE can be easily identified, when looking at the address bar, in front of it you should see a blue square with a white office building logo. This represents EMIE is enabled for this particular website.
The problem:
In this particular case we have setup EMIE, to use the Sitelist.xml hosted on a file server. It’s also possible to host the file on either a webserver or local file path.
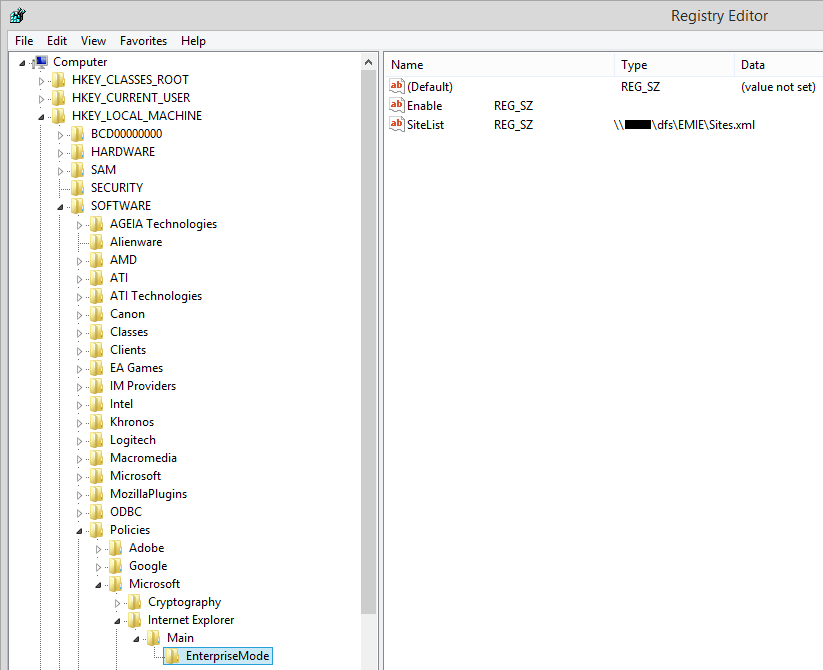
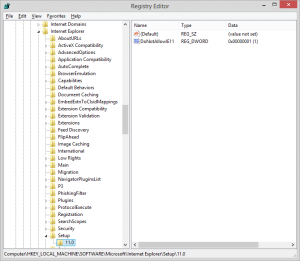
If we look at EMIE and it’s behavior in the registry, we can conclude the following information is necessary to configure EMIE for users.
In HKLM we encounter the following key and registry values: “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\EnterpriseMode” -Name “Enable” -value “blank” -type “REG_SZ”
And -Name “SiteList” -value “path to xml file” -type “REG_SZ”
figure 1.7: Regedit – HKLM
And in HKCU we encounter the following key and registry value: “HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\EnterpriseMode” -string “Currentversion” -value “1” -type “REG_SZ”
The currentversion value, checks if the Sitelist.xml has been updated between the previous and current session. If this is the case, EMIE will retrieve the new Sitelist.xml from the designated target location. This procedure also causes EMIE to malfunction in cases where the list has not been updated, but the list itself not being retrieved. The solution to this is to either delete the CurrentVersion value each time from the users registry, or to increase the version number within the Sitelist.xml. I choose another option: Use mandatory profiles! Since mandatory profiles is already in place within our environment, each time the user log’s out everything that is not preserved with RES Workspace Manager Zero Profile technology will be deleted. For more information about this particular ‘error’, please visit this social.technet thread.
What we encountered in our environment was that when logging in to a Citrix connected session the Enterprise Mode was not configured, opposed to when we logged in from an Remote Desktop Session. This has come forward during troubleshooting the issue. At first we looked with ProcMon to find if any other process was interfering with our Group Policy Object and RES Workspace Manager, which we use to configure HKCU Group Policy Objects and registry settings with, but we couldn’t find a direct lead to the problem.
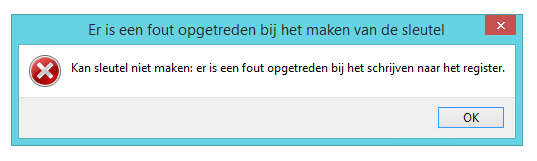
The behavior prior to resolving the issue was, that when using a Citrix connected session. The “EnterpriseMode” key was not and could not be created in the user’s registry for the length of the session. Strangely enough we could create registry value’s under .\Internet Explorer\Main, but not key’s. Regedit threw an error stating:
figure 1.8: Regedit – Error
Unfortunately the screenshot is in Dutch, but it states: Cannot create key: an error has occurred when trying to write to the registry
The workaround:
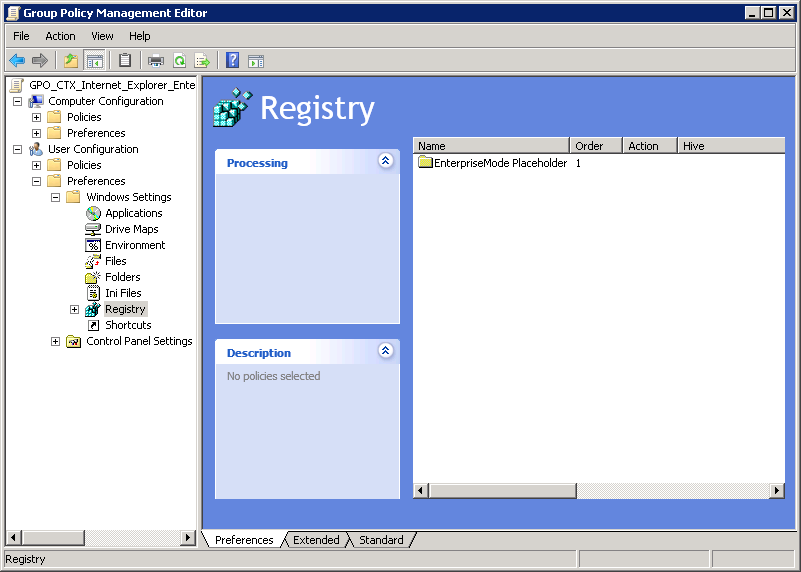
While troubleshooting, I’ve submitted a ticket with Microsoft Support, but they were unable to find anything concerning either Server 2012 R2, Internet Explorer and EMIE in particular. Which pointed me to Citrix. I received a tip from a Citrix partner to create a registry placeholder through Group Policy Object, which is what I did:
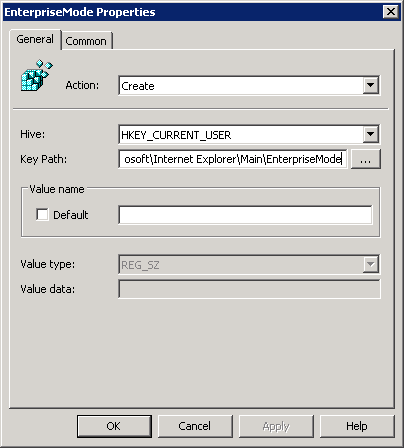
figure 1.9: Group Policy Objects – User Configuration registry placeholder
figure 1.10: Group Policy Objects – User Configuration registry placeholder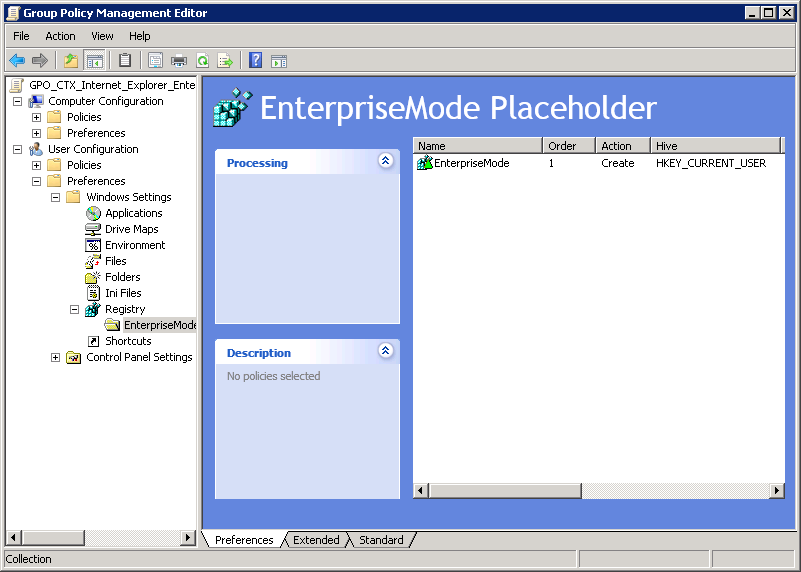
figure 1.11: Group Policy Objects – User Configuration registry placeholder
This finally ‘resolved’ my issue, and made it able to use EMIE within a Citrix XenApp 7.5 / 7.6 environment. However it’s still unclear what causes to hijack the “.\Internet Explorer\MAIN” key, due to the placeholder it’s now possible to create keys underneath MAIN which was necessary for EMIE to function properly.
Although this workaround works for now. I’m convinced the error lies within Citrix, and they should at least examine the root cause of this incident. Since Server 2012 R2 and Citrix XenApp is becoming common ground in Server Based Computing land, and I think it’s highly unlikely that no one else will encounter the same issue.
In the mean time, this should have to do the trick and I hope this can be useful for anyone encountering the same issue.
Don’t agree? Or got a better idea? -As always comments and contribution’s in the comment section are greatly appreciated.
Cheers! -Rens